An encryption method in which a key is required to encrypt data for storage and verify its integrity. Asymmetric key encryption uses public and private keys.

Asymmetric Cryptography An Overview Sciencedirect Topics
Digital Information Technology Mid-Term Study Guide 1.

. The reverse is also true. Symmetric encryption is the oldest and best-known technique. Asymmetric encryption is the strongest hashing algorithm which produces longer and more secure digests than symmetric encryption.
Which statement best describes key differences between symmetric and asymmetric cryptographic ciphers. In symmetric key encryption the same key is used for encryption and decryption where as asymmetric key uses private key for encryption and decryptionB. Asymmetric keys can be exchanged more securely than symmetric keys.
Section 4 Basic Cryptography Which two statements best describe the impact of cryptography on security investigations. It uses one single key for encrypting a message as well as decrypting it. With the increased legitimate usage of HTTPS traffic attackers have taken advantage of this blind spot to launch attacks over HTTPS more than ever before.
0 1 point Trudy deletes the message without forwarding it Trudy cannot read it because it is encrypted but allows it to be delivered to Bob in its original form Trudy reads the message Trudy changes the message and then forwards it on Incorrect Incorrect this material. What is an advantage asymmetric key encryption has over symmetric key encryption. A secret key which can be a number a word or just a string of random letters is applied to the text of a message to change the content in a.
Which scenario describes an integrity violation. Which of the following statement correctly describes the difference between symmetric key encryption and asymmetric key encryption. Asymmetric key encryption uses public and private keys.
It is smaller than or equal to the size of the original plain text. Which statement describes asymmetric encryption algorithms. Which statement best describes key differences between symmetric and asymmetric cryptographic ciphers.
They are also. The reverse is also true. Which of the following statements best describes asymmetric key encryption.
If a public key encrypts the data the matching private key. It uses two different keys- one for encryption and another for decryption of a message. A cryptographic security mechanism that uses the same key for both encryption and decryption.
A symmetric encryption algorithm uses an identical key for both encryption and decryption. To use symmetric-key encryption each user needs two different keys b. Asymmetric algorithms use two keys.
Which statement best describes asymmetric-key encryption. Alice sends a message to Bob that is intercepted by Trudy. They have key lengths ranging from 80 to 256 bits.
A public key and a private key. They include DES 3DES and AES. Symmetric encryption is used for confidentiality and uses the same key for encryption and decryption.
If a private key is used to encrypt the data a private key must be used to decrypt the data. Data encrypted with the public key can only be decrypted using the private key. Cryptographic attacks can be used to find a weakness in the cryptographic algorithms.
An encryption method in which the same key is used to encrypt and decrypt a message. Symmetric key encryption uses only one key both to encrypt and decrypt data. Which of the following statements best describes the properties of public key encryption.
1Which of the following statements best describes asymmetric key encryption. Study sets textbooks questions. Public key encryption is an encryption method which relies on separate keys for encrypting and decrypting information.
Select a correct statement regarding encryption methods. Which of the following statement correctly describes the difference between symmetric key encryption and asymmetric key encryptionA. Asymmetric key encryption is harder to break than symmetric key encryption.
Asymmetric encryption is primarily used for confidentiality and uses different keys for encryption and decryption. Asymmetric encryption also called asymmetric-key encryption or public-key encryption refers to an encryption method in which two keys are used to encrypt and decrypt a message. The organization will need.
The secret key that is used must be sent over a secure channel to the intended recipientIn the symmetric algorithm data is converted to a form that can only be decrypted by someone who has the secret key. Data encrypted with the public key can only be decrypted using the private key. An encryption method in which two separate keys -- a private key and a public key -- are used to encrypt and decrypt a message.
In symmetric encryption the same key is used for encryption and decryption. The public key is known to all sending and. BA cryptographic security mechanism that uses public and private keys to encrypt and decrypt data.
CA cryptographic security mechanism that uses. Which of the following statements best describes asymmetric key encryption. Symmetric encryption is faster and more efficient as compared.
Which statement best describes configuring a NAT router to use dynamic mapping. Both symmetric-key and asymmetric-key encryption methods require the involvement of a certificate authority d. A private key and a public key.
Most companies prefer using symmetric-key encryption than asymmetric-key encryption method c. Symmetric encryption is used for confidentiality and uses the same key for encryption and decryption. AA cryptographic security mechanism that uses two separate sets of public and private keys to encrypt and decrypt data.
Both keys are capable of the encryption process but the complementary matched key is required for decryption. Symmetric Key Encryption. Symmetric encryption is the oldest and best-known.
An asymmetric encryption algorithm uses two keys namely a public key and a private key. Asymmetric Key Encryption.

Si110 Asymmetric Public Key Cryptography
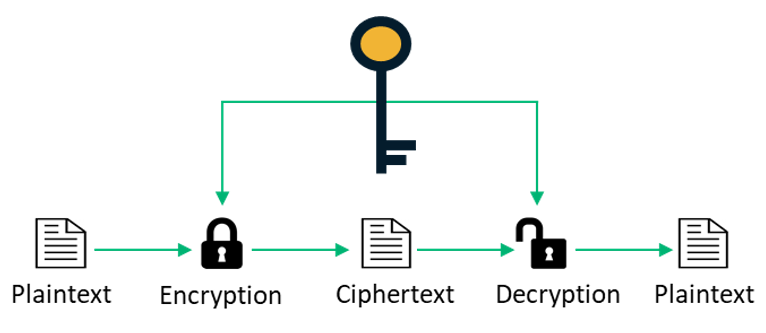
Symmetric Vs Asymmetric Encryption 5 Differences Explained By Experts
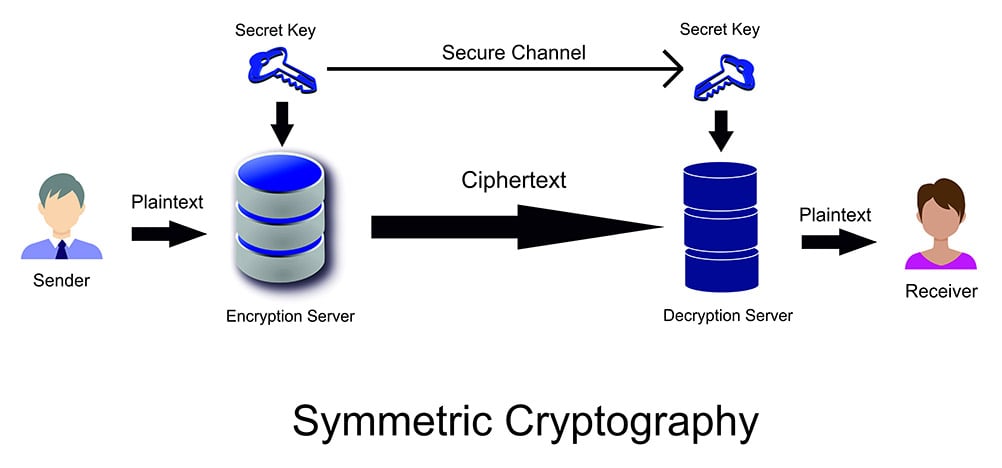
Symmetric Vs Asymmetric Encryption What S The Difference
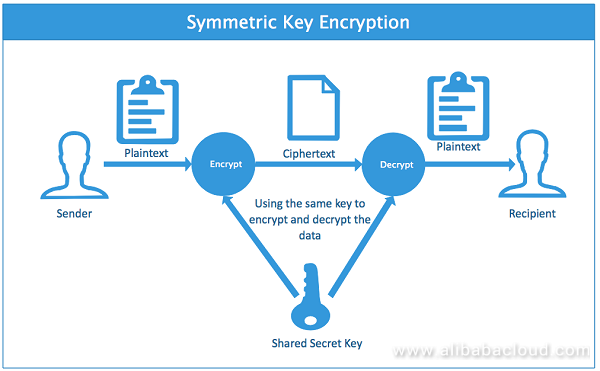
Sql Server Best Practices Using Asymmetric Keys To Implement Column Encryption By Alibaba Cloud Medium
0 Comments